Kibana 7.8.x and older
User manual for ReadonlyREST Enterprise/PRO/Free plugins
Kibana Plugin overview
ReadonlyREST plugin for Kibana is not open source, and it's offered as part of the ReadonlyREST PRO and ReadonlyREST ENTERPRISE, and ReadonlyREST Free packages. See product descriptions and a comparison chart in the official ReadonlyREST website
ReadonlyREST plugins for Kibana always require ReadonlyREST Free to be installed in the Elasticsearch nodes your Kibana instance(s) will connect to.
It's not mandatory to install ReadonlyREST Free in all Elasticsearch nodes, but only in the ones in where you need the HTTP interface to be secured.
After purchasing
You will receive a link to the plugin zip file in an email. Download your zip.
You will be able to download it also in the future as long as your subscription is active.
Version strings
All our plugins include in their file name a version string. For example the file readonlyrest-1.16.26_es6.4.0.zip has a version string 1.16.26_es6.4.0.
Reading version strings
Given the version string 1.16.26_es6.4.0
ReadonlyREST plugin code version
1.16.26Works only with Elasticsearch/Kibana version
6.4.0
The "es" stands for "Elastic stack" which used to mean the family of products made by Elastic which get released at the same time under the same version number. This was chosen before Elastic renamed their X-Pack commercial offer to Elastic Stack.
To be clear, there is no affiliation between ReadonlyREST and Elastic, or their commercial products.
Trial builds version strings
Trial builds are valid for 30 days after they were built, and they will stop working soon after the time is elapsed. Trial builds have a special version string which includes a build-time timestamp.
I.e. readonlyrest_kbn_pro-1.16.26-20180911_es6.0.0.zip
ReadonlyREST PRO plugin version 1.16.26
Build date 11th September 2018, expiring on the 11th of October 2018.
Works only with Kibana version 6.0.0
When an update is out
You will receive another email notification that a new deliverable is available.
If the update contains a security fix, it is very important that you take action and update the plugin immediately.
Installation
You can install this as a normal Kibana plugin using the bin/kibana-plugin utility.
Install via URL
This installation method is more practical if your Kibana server is connected to the internet.
According to what edition of ReadonlyREST you want to install, from your Kibana installation, launch one of the commands:
Please note that this will always download the latest version of Kibana plugin available for the current supported Elasticsearch version.
If you want to download the latest version of plugin for a specific version of Elasticsearch, then use query parameter esVersion to specify your required Elasticsearch version.
If you want to download an older version of plugin for a specific version of Elasticsearch, then use query parameter pluginVersion along with esVersion.
If you are a PRO or Enterprise subscriber, the link will include an extra parameter "token" which can only be used in association with the provided email address.
You can append required plugin version and Elasticsearch version query parameters to download specific version as described above.
NB: This URL is personal, and should be handled as a secret.
You can obtain official links with personal secret tokens using our self service download form, once your email address has been recognized as active subscriber.
Install from zip file
Notice how we need to type in the format file:// + absolute path (yes, with three slashes).
Uninstall
Upgrade
Just uninstall the old version and install the new version.
Install the new version of ReadonlyREST into Kibana.
Restart Kibana.
Using ROR with a reverse proxy
ROR - just like Kibana itself - is meant to be used either with a proxy or without one, but not both simultaneously. If you decide to set the server.basePath property in kibana.yml be sure to access RoR via a proxy, as it will not work properly when accessed directly.
Configuration
ReadonlyREST for Kibana is completely remote-controlled from the Elasticsearch configuration. Login credentials, hidden Kibana apps, etc. are all going to be configured from the Elasticearch side via the usual "rules". This means the configuration will be kept all in one place and if you used ReadonlyREST before , it will be also very familiar.
In this document, every time you will encounter references to "readonlyrest.yml" or "elasticsearch.yml", we will be referring to the configuration files in the Elasticsearch plugin (our Kibana plugins do not need a "readonlyrest.yml").
In general, by design, we tend to concentrate all configuration within the main plugin (the Elasticsearch one) as much as possible.
Clusterwide Settings vs readonlyrest.yml
(PRO)
Our Kibana plugins introduce a "ReadonlyREST" Kibana app. From here, you can edit the security settings of the whole Elasticsearch cluster, and they will take effect within 10 seconds in all Elasticsearch cluster nodes without the need to restart them.
When you change the security settings from the Kibana app, they will be saved in a special index called ".readonlyrest", so all the Elasticsearch nodes will pick them up. You can customize a name of the index by setting readonlyrest.settings_index: .my_custom_readonlyrest in elasticsearch.yml file (remember to set the same value for all your ES nodes).
When an Elasticsearch node restarts, the order of settings evaluation is the following: 1. Attempt to find valid settings in readonlyrest.yml 2. If none is found, look inside elasticsearch.yml 3. Once successfully bootstrapped using file-based settings, attempt to read ".readonlyrest" index 4. If the index exists and contains valid settings, override file based settings with the ones from the index. 5. Pressing "save" in the cluster wide settings app, will not overwrite the readonlyrest.yml file.
Best practices:
Build and update your production security settings from the Kibana app (will be saved in index)
Protect the ".readonlyrest" Kibana index with an ACL rule
Loading settings: order of precedence
As you read, there are two possible places where the settings can be read from:
readonlyrest.ymla file the user needs to create in the same directory whereelasticsearch.ymlis found..readonlyrestindex. Our Kibana plugins' GUI (PRO/Enterprise) is programmed to write this index.
When the ES plugin boots up, it follows some logic to evaluate where to read the YAML settings from. The following diagram shows how that works.

Malformed in-index settings
If for some reason the in-index settings get corrupted and ROR can't parse them, then neither settings from file or in-index settings can be loaded, so ES can't start. In this case ES would print message like:
To recover from this state, set readonlyrest.force_load_from_file: true in elasticsearch.yaml on one node es1.
Example recovery settings:
elasticsearch.yaml
readonlyrest.yaml
Then remove in-index settings index manually.
Now you can restore your settings to readonlyrest.yml, remove readonlyrest.force_load_from_file: true from elasticsearch.yaml and restart node.
Example: multiuser ELK
Make sure X-Pack is uninstalled or disabled from elasticsearch.yml (on the Elasticsearch side) and kibana.yml (on the Kibana side): This is how you disable X-pack modules:
This is a typical example of a configuration snippet to add at the end of your readonlyrest.yml (the settings file of the Elasticsearch plugin), to support ReadonlyREST PRO.
Very important
Whatever your configuration ends up being, remember:
The admin user has
kibana.access: adminRemember to use
kibana.hide_apps: ["readonlyrest_kbn"]to hide the ReadonlyREST icon from who is not meant to use it (makes for a better UX).
Rules ordering matters
Blocks related to the authentication of the users should be at the top of the ACL
One of the most common mistakes is forgetting that the ACL blocks are evaluated in order from the first to the last.
So, some request with credentials can be let through from one of the first blocks and come back to Kibana with no user identity metadata associated.
Take this example of troublesome ACL:
The user will be able to login because the login request will be allowed by the first ACL block. But the ACL will not have resolved any metadata about the user identity (credentials checking was ignored)!
This means the response to the Kibana login request will contain no user identity metadata (username, hidden apps, etc) and ReadonlyREST for Kibana won't be able to function correctly.
The solution to this is to reorder the ACL blocks, so the ones that authenticate Kibana users are on the top.
Session cookie expiration
When a user logs in, ReadonlyREST will write an encrypted cookie in the browser. This cookie has an time to live that can be tweaked with the following configuration key in kibana.yml.
Clearing Session History
By default, all the session data like search history, dev tool commands history, etc, will be wiped out from the browser whenever a new user is logged in, or a user changes tenancy. To override this behaviour, use this setting:
Possible values: "login", "tenancyHop", "never".
Kibana App strings
Examples of valid arguments for the kibana.hide_apps: [...] rule (readonlyrest.yml)
readonlyrest_kbn (obsolete)
ReadonlyREST
Kibana configuration
Activate authentication for the Kibana server: let the Kibana daemon connect to Elasticsearch using a pair of credentials we just defined in readonlyrest.yml (see above, the ::KIBANA-SRV:: block).
Open up conf/kibana.yml and add the following:
And of course also make sure elasticsearch.url points to the designated Elasticsearch instance (check also the http or https)
Proxy Auth
ROR for Elasticsearch can delegate authentication to a reverse proxy which will enforce some kind of authentication, and pass the successfully authenticated user's name inside a X-Forwarded-User header.
Today, it's possible to skip the regular ROR login form and use the "delegated authentication" technique in ROR for Kibana as well.
Configure ROR for ES to expect delegated authentication (see
proxy_authrule) in ROR for ES documentation.Open up
conf/kibana.ymland addreadonlyrest_kbn.proxy_auth_passthrough: true
Now ROR for Kibana will skip the login form entirely, and will only require that all incoming requests must carry a X-Forwarded-User header containing the user's name. Based on this identity, ROR for Kibana will build an encrypted cookie and handle your session normally.
Custom Logout link
Normally, when a user presses the logout button in ROR for Kibana, it deletes the encrypted cookie that represents the users identity and the login form is shown.
However, when the authentication is delegated to a proxy, the logout button needs to become a link to some URL capable to unregister the session a user initiated within the proxy.
For this, ROR for Kibana offers a way to customize the logout button's URL:
Find a link that will delete the reverse proxy's user session
Open up
conf/kibana.ymland addreadonlyrest_kbn.custom_logout_link: https://..../logout
Now users that gained a session through delegated auth, can also click on the logout button in ROR for kibana and actually exit their session.
Custom Login link
When you delegate authentication to an external service, you can tell ReadonlyREST to skip the classic login form entirely and redirect users to your proxy or identity provider's login screen.
To enable this:
Find your authentication proxy or identity provider login URL for the ROR app
Open up
conf/kibana.ymland addreadonlyrest_kbn.custom_login_link: "https://../login"
The advantage of this approach is a streamlined user experience for users that login with an external IdP. The disadvantage is that you give up the possibility to login as a local user in ROR, as the login form will be always skipped.
Caveat
Enabling proxy auth passthrough will relax the requirement to provide a password. Therefore, don't enable this option if you don't make sure Kibana can only be accessed through the reverse proxy*.
JWT Token Forwarding as URL Query Parameter
Alternatively to typing in credentials in the standard login form, it is possible to create an authenticated Kibana session by passing a JWT token as a query parameter in a URL.
Configuration
To enable this feature in ReadonlyREST, you need to:
Have JWT authentication configured in ReadonlyREST (modifying
readonlyrest.ymlor the cluster wide settings UI in the Kibana plugin). See how.Specify the query parameter name in
kibana.ymlby adding the linereadonlyrest_kbn.jwt_query_param: "jwt"as a string, in our case "jwt".
In Action
Once Kibana is restarted, you will be able to navigate to a link like this:
The following will happen:
The Kibana plugin will forward the JWT token found in the query parameter into the
Authorizationheader in a request to Elasticsearch.Elasticsearch will cryptographically authenticate and resolve the user's identity from the JWT claims.
Kibana will write an encrypted cookie in your browser and use that from now on for the length of the authenticated session. From here onwards, the session management will be identical to the normal login form flow.
When the user presses logout, Kibana will delete the cookie and redirect you to the login form, or whatever link you configured as
readonlyrest_kbn.custom_logout_link.
Deep linking with JWT
Because the identity is embedded in the link, and ReadonlyREST is able to authenticate the call on the fly, the JWT authentication can be used in conjunction with nextUrl query parameter for sharing deep links inside Kibana apps, or embedding visualizations and dashboards inside I-Frames.
Anatomy of a JWT deep link
In Javascript one can compose a JWT deep link as follows:
The result may look something like this:
Audit log
The audit log feature is widely described in 📖docs for Elasticsearch plugin. Kibana plugin has predefined dashboard representing collected audit data.
Loading visualization
In the Audit tab of the ReadonlyREST Kibana app, there is a button that automatically creates a dashboard with some audit log specific visualizations.

Click the Load button to load the dashboard and visualizations. An Override checkbox allows to reload the default dashboard and visualizations. It will override any previously loaded audit log dashboard.

In detail, this feature creates three Kibana "saved objects":
an index pattern for
readonlyrest_audit-*a dashboard called
ReadonlyREST Audit Logsome visualizations
Dashboard
The audit log dashboard, by default, has only a few basic visualizations. They cover security, access logs, and performance metrics.
SAML
ReadonlyREST Enterprise supports service provider initiated via SAML. This connector supports both SSO (single sign on) and SLO (single log out). Here is how to configure it.
Configure ReadonlyREST ES bridge
In order for the user identity information to flow securely from Kibana to Elasticsearch, we need to set up the two plugin with a shared secret, that is: an arbitrarily long string.
Elasticsearch side
Edit readonlyrest.yml
There are three rule types available, depending on what you want to achieve:
ror_kbn_authentication (handles only authentication)
ror_kbn_authorization (handles only authorization)
ror_kbn_auth (authentication + authorization in a single rule)
⚠️IMPORTANT the Basic HTTP auth credentials for the Kibana server are still needed for now, due to how Kibana works.
Kibana side
Edit kibana.yml and append:
issuer: issuer string to supply to identity provider during sign on request. Defaults to 'ror'disableRequestedAuthnContext: if truthy, do not request a specific authentication context. This is known to help when authenticating against Active Directory (AD FS) servers.decryptionPvk: Service Provider Private Key. Private key that will be used to attempt to decrypt any encrypted assertions that are received.cert: The downloadable certificate in IDP Metadata (file, absolute path)
For advanced SAML options, see passport-saml documentation.
Identity provider side
Enter the settings of your identity provider, create a new app.
Configure it using the information found by connecting to
http://my.public.hostname.com/ror_kbn_sso_saml_serv1/metadata.xml
Example response:
Create some users and some groups in the identity provider app
Check the user profile parameter names that the identity provider uses during the assertion callback ( TIP: set kibana in debug mode so ReadonlyREST will print the user profile).
Match the name of the parameter used by the identity provider to carry the unique user ID (in the assertion message) to the
usernameParameterkibana YAML setting.If you want to use SAML for authorization, take care of matching also the
groupsParameterto the parameter name found in the assertion message to the kibana YAML setting.
OpenID Connect (OIDC)
ReadonlyREST Enterprise support OpenID Connect for authentication and authorization.
soon we will create a specific guide only for OpenID, like the ones we have for SAML
Here is how to configure it.
Configure ReadonlyREST ES bridge
This part is identical as seen in SAML connectors. In order for the user identity information to flow securely from Kibana to Elasticsearch, we need to set up the two plugin with a shared secret, that is: an arbitrarily long string.
Elasticsearch side
Edit readonlyrest.yml
There are three rule types available, depending on what you want to achieve:
ror_kbn_authentication (handles only authentication)
ror_kbn_authorization (handles only authorization)
ror_kbn_auth (authentication + authorization in a single rule)
⚠️IMPORTANT the Basic HTTP auth credentials for the Kibana server are still needed for now, due to how Kibana works.
If you have configured OIDC with the groupsParameter ( See below ), you can also restrict ACL to specific groups:
You may also use any custom claim from the OIDC userinfo token in ACL rules by using {{jwt:assertion.<path_to_your_claim>}} syntax. See the Dynamic variables from JWT claims section for more information. ( TIP : Do not forget the assertion prefix in front of you jsonpath. )
Kibana side
We will assume the OpenID identity provider responds to port 8080 of localhost. In our example, we used Keycloak, an open source implementation of OpenID Connect identity provide.
Edit kibana.yml and append:
Identity provider side
Enter the settings interface of your identity provider, and create a new OpenID app .
The redirect URL should be configured as
http://localhost:5601/*assuming kibana is listening on localhost and on the default port.Create some users and some groups in the identity provider if not present.
Check the user profile parameter names that the identity provider uses during the assertion callback ( TIP: set readonlyrest_kbn.logLevel: debug` in kibana.yml, so you will see the user profile how it's received from the identity provider right in the logs).
Match the name of the parameter used by the identity provider to carry the unique user ID (in the assertion message) to the
usernameParameterkibana YAML setting.If you want to use OpenID for authorization, take care of matching also the
groupsParameterto the parameter name found in the assertion message to the kibana YAML setting. ( TIP: thegroupsParametermust be present in theuserinfotoken of your OIDC provider.)If kibana is accessed through a reverse proxy, kibanaExternalHost should be configured with the external hostname. if omitted, the default value is equals to
server.host:server.portdefined in kibana.yml. ( This parameter can be used also when kibana is bound to 0.0.0.0, for example, if using docker.)
Load balancers
Enable health check endpoint
Normally a load balancer needs a health check URL to see if the instance is still running, you can whitelist this Kibana path so the load balancer avoids a redirection to /login.
Edit kibana.yml
Session management with multiple Kibana instances
Each Kibana node stores user sessions in-memory. This will cause problems when using multiple Kibana instances behind a load balancer (especially without sticky sessions), as there would be no synchronization between nodes' sessions cache. To avoid this, session synchronization via an Elasticsearch index should be enabled. Follow these steps:
Come up with a string of at least 32 characters length or more to be used as the shared cookie encryption key, called
cookiePass.Open up
conf/kibana.ymland add:readonlyrest_kbn.cookiePass: "generatedStringIn1step"(example: "12345678901234567890123456789012")readonlyrest_kbn.cookieName(custom cookie name - this property is optional, if not specified default cookie name would berorCookie)readonlyrest_kbn.store_sessions_in_index: true(enable session storage in index)readonlyrest_kbn.sessions_index_name: "someCustomIndexName"(index name - this property is optional, if not specified default index would be.readonlyrest_kbn_sessions)readonlyrest_kbn.sessions_refresh_after: 1000(time in milliseconds, describes how often sessions should be fetched from ES and refreshed for each node - optional, by default 2 seconds)readonlyrest_kbn.sessions_probe_interval_seconds: 15(default 10s) how often should the browser poll Kibana to check if their session is still valid. Raise this value if you connect to Kibana through slow networks (i.e. VPN), or have very slow loading dashboards.
Add the above config in all Kibana nodes behind the load balancer, and restart them.
Login screen tweaking
(PRO)
It is possible to customize the look of the login screen.
Two column layout
By default,the login form appears in a single column view.
But once title and subtitle are configured, it will switch to two columns for making room to the new text.
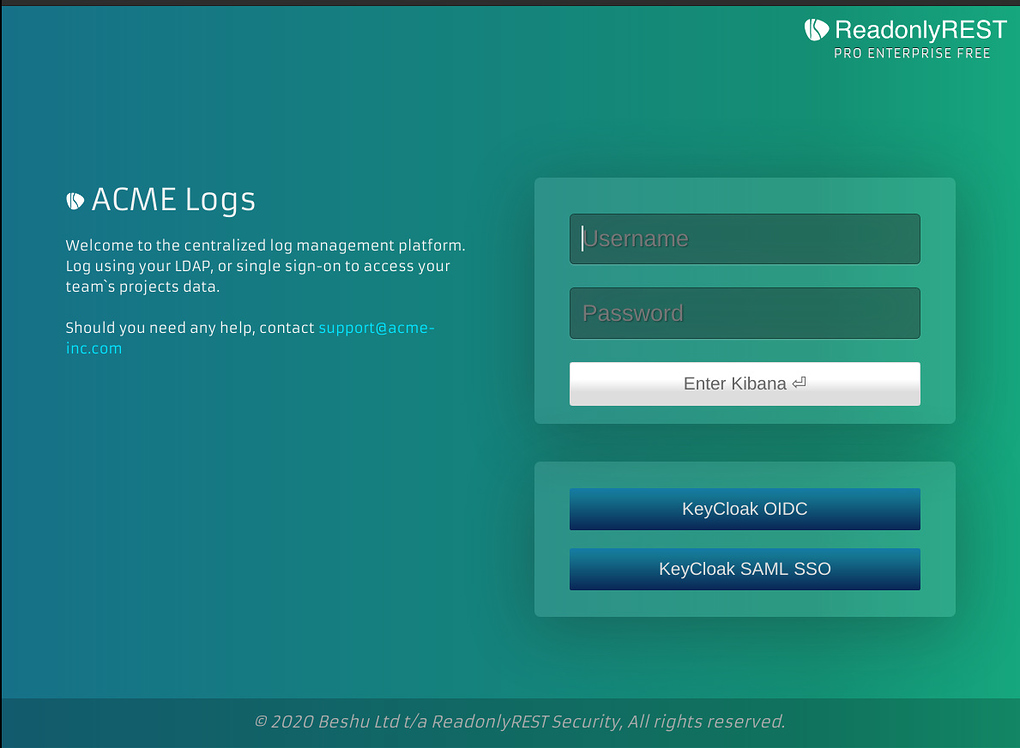
Add your company logo
It's recommended to use a transparent PNG, negative logo. Ideally a white foreground, and transparent background.
Open config/kibana.yml and append the following:
Add custom CSS/JS
You have the opportunity to inject HTML code right before the closing head tag (</head>).
Open config/kibana.yml and append the following:
Kibana UI tweaking
With ReadonlyREST Enterprise, it's possible to inject custom CSS and Javascript to achieve a customized user experience for your users/tenants.
Inject custom CSS in Kibana
Open config/kibana.yml and append the following:
Alternatively, it's possible to load the CSS from a file in the filesystem:
Inject custom JS in Kibana
Map groups to aliases
You can provide a function, mapping group IDs to aliases of your choosing. To do so, add the following line to config/kibana.yml:
⚠️IMPORTANT The mapping function has to return a string. Otherwise, an error will be printed in kibana logs and the original group ID will be used as fallback. Also, if the mapping function is not specified, the original group ID value will be used.
Tenancy index templating
When a tenants logs in for the first time, ReadonlyREST Enterprise will create the ".kibana" index associated to the tenancy. For example, it will create and initialize the ".kibana_user1" index, where "user1" will store all the visualizations, dashboards, settings and index-patterns.
The issue is that "user1"'s user experience will be really raw as they will see a completely blank Kibana tenancy. Not even a default index pattern will be present. And this is particularly challenging if the tenant is supposed to be read-only (i.e. kibana_access: "ro") because they won't even have privileges to create their own index-pattern, let alone any dashboards.
To fix this, ReadonlyREST Enterprise offers the possibility for administrators to create a template kibana index from which all the Kibana objects will be copied over to the newly initialized tenancy.
How to use tenancy templating
An administrator will need to create the template tenancy, populate it with the default Kibana objects (index-patterns, dashboards) and configure ReadonlyREST Enterprise to take the index template it in use. Let's see this step by step:
Create the template tenancy
Let's start to add to our access control list (found in $ES_PATH_CONF/config/readonlyrest.yml, or ReadonlyREST App in Kibana) a local user "administrator" that will belong to two tenancies: the default one (stored in .kibana index), and the template one (stored in .kibana_template index).
NB: If you know what you are doing, you can add a tenancy with kibana_index: ".kibana_template" adding a LDAP/SAML group to your administrative user.
Configure the template tenancy
Now login as administrator in Kibana, hop into the "Template" tenancy, and start configuring the default UX for your future tenants. Add all the index patterns, create or import all the dashboards you want.
Configure the template tenancy index in ReadonlyREST Enterprise
Open kibana.yml and add the following line:
Now, ReadonlyREST Enterprise will look for the ".kibana_template" index, and try to copy over all its documents every time a new kibana index is initialized to support a new tenancy.
Try it out
Restart Kibana with the new setting. Add a new tenancy to the ACL:
Now try to login as user1, and ReadonlyREST Enterprise should initialize the index ".kibana_user1" with all the index patterns and dashboards contained in the template tenancy.
Last updated
